News
Definition and How It Works
What Is Distributed Ledger Technology (DLT)?
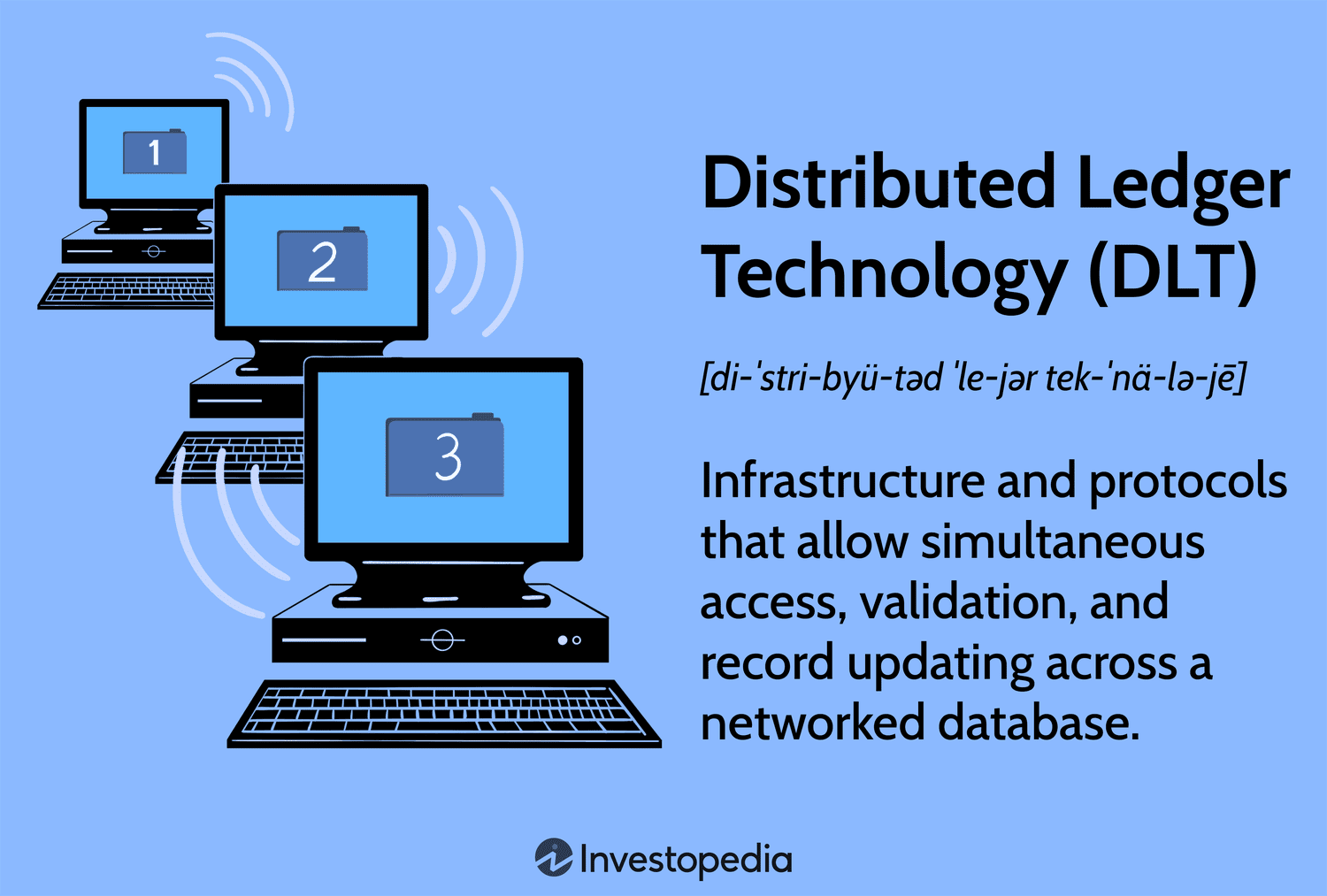
Distributed ledger technology (DLT) is the technological infrastructure and protocols that allow simultaneous access, validation, and record updating across a networked database. DLT is the technology blockchains are created from, and the infrastructure allows users to view any changes and who made them, reduces the need to audit data, ensures data is reliable, and only provides access to those that need it.
Key Takeaways
- Distributed ledgers are maintained by a network of nodes, each of which has a copy of the ledger, validates the information, and helps reach a consensus about its accuracy.
- Distributed ledgers have been around for decades but have become more well-known, researched, used, and developed since Bitcoin was introduced.
- Distributed ledgers can be used in nearly every industry where data is collected and used.
- All blockchains are distributed ledgers, but not all distributed ledgers are blockchains.
- Though DLT enhances accountability, security, and accessibility, it is still complex and difficult to scale.
History of Distributed Ledgers
Distributed computing is not new—businesses and governments have been using the concept for several decades. In the 1990s, it became possible for multiple computers and users in different locations to solve problems and return the solutions to a central location.
Advances in data science, computing, software, hardware, and other technologies have made ledgers much more capable. Improved connectivity through intranet and internet protocols allowed for much more data to be collected, analyzed, and used. However, because there can now be many users with access to data, it is necessary to have someone verify the changes.
Computer and data scientists developed programs that reduced the need for auditing data. These programs used automation and data encryption techniques to verify database transactions or changes in a database’s state. This is called consensus—the act of automated majority agreement on transaction validity, where a transaction is simply a change made to a database’s state.
Distributed ledgers evolved into scalable and programmable platforms, as seen in Ethereum and HyperLedger, where solutions can be created to use a database, or ledger, for everything from tokenizing physical assets to streamlining manufacturing and other business processes.
How Distributed Ledger Technology Works
DLTs allow information to be stored securely and accurately using cryptography. The data can be accessed using “keys” and cryptographic signatures. Once the information is stored, it can become an immutable database; the rules of the network, written into the coding of the database programming, govern the ledger.
If something is immutable, it is unable to be changed. Distributed ledgers are only immutable if they are programmed to be that way. Blockchains are immutable because they are decentralized and cryptographically enhanced public ledgers.
Because they are decentralized, private, and encrypted, distributed ledgers are less prone to cybercrime, as all the copies stored across the network need to be attacked simultaneously for the attack to be successful. Additionally, the peer-to-peer sharing and updating of records make the whole process much faster, more effective, and cheaper.
Every device on a distributed ledger network stores a copy of the ledger. These devices are called nodes—a network can have any number of nodes. Any changes to the ledger, such as moving data from one block to another, are recorded across all nodes. Because each node has a copy of the ledger, each one publishes its version with the latest transactions.
If the network reaches a consensus about the validity of the latest ledger, the transactions are finalized, encrypted, and used as a basis for the following transactions. This is how blockchains develop—each block contains encrypted information about the proceeding block, which makes them impossible to change.
Industries Using Distributed Ledger Technology
Distributed ledgers are created for many different purposes, but one of the most used ways is as a platform for others to scale and use. One of the more well-known distributed ledgers is Hyperledger Fabric. It is a modular and scalable DLT platform several businesses have used to create solutions that span many industries. Some industries that have implemented DLT solutions include aviation, education, healthcare, insurance, manufacturing, transportation, and utilities.
Supply chains can benefit greatly from DLT. Many factors make them inefficient, inaccurate, and susceptible to corruption or losses. Fujitsu, a global data and information technology company, has designed distributed ledger technology to enhance supply chain transparency and fraud prevention by securing and tracking data.
Fujitsu’s Rice Exchange was created to trade rice, ensuring data regarding sources, prices, insurance, shipping, and settlement are recorded on the ledger. Anyone involved can look at any data and find accurate information regarding the entire process because it cannot be changed. All data is entered and secured automatically by the platform—it will eventually provide tracking information for rice shipping containers as it is shipped to its final destination.
Uses of Distributed Ledger Technology
Aside from specific industries, there are also specific situations where DLT solutions have proven to add value. Some examples of specific DLT uses include:
- Record transactions: DLT enables secure, transparent, and decentralized transactions without the need for a central authority. As DLT is a ledger, it records inputs and outputs. Though this naturally lends itself to financial records, DLT can record any type of transaction, not just financially based ones.
- Secure identities: DLT can be used to create a secure and tamper-proof digital identity for individuals, as the technology can provide a reliable way to verify identities and prevent identity theft.
- Collect votes: DLT can be used to create a secure and transparent voting system that can prevent voter fraud and ensure the integrity of the voting process. As mentioned above, as transactions (financial or non-financial) are recorded, a transparent, immutable, open ledger of interactions with users is saved. This enhances the equity and believability of a collection of opinions.
- Enter contracts: DLT allows for smart contracts, agreements that automatically execute or complete based on prevailing conditions. For example, an insurance claim may automatically release funds once the claim has been processed. This limits error and DLTs make it more difficult for precarious activity by bad actors.
- Demonstrate ownership: DLT can be used to record property transactions, creating a tamper-proof and transparent record of ownership and transfer of property. Though there are some limitations on translating real-world ownership of physical assets to a distributed ledger, the ledger may be able to convey an unchangeable source of truth regarding ownership.
DLT may also be referred to as a shared ledger as it requires a ledger to be shared across a peer-to-peer computer network.
Advantages and Disadvantages of Distributed Ledger Technology
Pros of DLT
DLT holds many benefits over more traditional centralized ledger systems. Because DLT is a decentralized system, there is no central point of control or failure. This makes DLT more resilient to attacks and less vulnerable to system-wide failures. Also, because DLT uses cryptographic algorithms to secure data, it is nearly impossible to tamper with or forge records. This enhances the trustworthiness of the data and reduces the risk of fraud.
DLT allows for transparent access to data and transactions, allowing all users greater visibility into the operations of the system. This may lead to greater buy-in from users due to transparency and accountability of records.
DLT can streamline processes by removing intermediaries and automating transactions through smart contracts. Because smart contracts may automatically execute when contract conditions are met, there may be less need for human interaction or administration. This can reduce costs and increase efficiency.
Last, DLT can enable greater financial inclusion. Some people may not have access to traditional banking services. As DLT often relies only on an internet connection, individuals who would be otherwise limited may have access to a greater range of services. This extends to the use of different platforms and networks via interoperability.
Cons of DLT
Due to DLT’s infancy, there are still considerable downsides to the technology. DLT is still complex and difficult to implement and maintain. Leveraging the solution often requires specialized knowledge and expertise, especially to implement.
DLT can struggle with scalability as the number of participants and transactions increases. As a result, DLT processes may lead to slower processing capabilities or higher use costs. In addition, some DLTs such as Bitcoin require a significant amount of energy to maintain the network and process transactions. This can have negative environmental impacts.
As seen by the actions of bad actors, the lack of regulation and standardization in the blockchain industry (blockchains are derived from DLT) can lead to risk for users and investors. By extension, DLT requires widespread adoption to be effective, and many industries and organizations may be hesitant to adopt new technologies due to these security concerns.
Distributed ledgers might be immutable, but this benefit also comes with a significant downside—if mistakes are made, they cannot be changed unless there are users with permission to do so. In a public DLT like the Bitcoin blockchain, this can be problematic. For instance, if a user typed an erroneous address in their wallet and sent the wrong person some Bitcoin, they cannot reverse the transaction.
Pros
-
Spreads systematic risk around, minimizing the risk of a single point of failure
-
Has greater security due to cryptographic algorithms
-
Allows for transparency and visibility into operations
-
May prove to be more efficient due to smart contract automation
-
Offers individuals with limited access to traditional systems potentially greater capabilities
Cons
-
Is more complex compared to traditional ledger solutions
-
Can require higher energy consumption for operation
-
May have difficult scaling as more users/transactions occur
-
Some applications remain risky due to lack of regulation
-
May prove to be difficult to reverse fraudulent or erroneous activity
Why Distribute Ledger Technology Is Important
DLT is important because it has the potential to transform how information is recorded, stored, and distributed. The importance is often cited across three pillars: security, transparency, and accessibility.
Security
Traditional ledger technology often has a central point of control, with one single entity often in charge of the ledger. DLT makes the ledger more resilient to attacks and less vulnerable to system-wide failures. As DLT uses cryptographic algorithms to secure data, it also makes it more difficult to tamper with or forge records.
Consider a traditional banking system where a banker is the central point in ensuring your transaction is recorded correctly. In contrast, consider a DLT solution built on a consensus mechanism where all distributed ledgers must be in agreement about how a transaction is recorded. This validation of transactions allows greater trust among users and removes the power an individual might have to alter data.
Transparency
Centralized, traditional ledgers often restrict access to specific individuals. Though this still holds value for sensitive information, there are many use cases where it is more beneficial for all when data and information are broadly distributed and transparent. Consider the example above of voting; having digitally distributed, undisputable, verifiable records of voting may enhance the believability of results.
DLT is also important as it holds the theory of reducing fraud and increasing accountability in the long term. Note how all transactions within a DLT system are able to be viewed by anyone with access to the DLT. The information may be “audited” by anyone at any time, potentially demotivating bad actors from entering into nefarious activity in such a public sphere.
Accessibility
Last, DLT may eventually be critically important to developing and emerging countries or regions where centralized technologies are limited. Think about the banking limitations of different countries around the world. DLT boasts the ability to store and record transactions using only a network connection as opposed to a very niche (and expensive) connection, such as a bank account at a specific bank.
As DLT is a relatively new technology that is still being explored and developed, this presents opportunities for innovation and the creation of new applications and use cases. In general, because of the ease of being to access DLT solutions, there are many positive implications on the broad public being able to communally access a shared network with often fewer bureaucratic hurdles to meet prior to access.
Distributed Ledger Technology Consensus Mechanisms
A central facet of DLT is how transactions are “approved” when consensus needs to be reached among a disparate user base. Without a universally-agreed system of how items are accepted within the DLT, users of the DLT would be unable to universally agree on how items to include and what items should be excluded.
This process of reviewing transactions is called a consensus mechanism, and a DLT may leverage any of the following processes. Note that consensus mechanisms are constantly evolving, and only several of the more common approaches are listed below:
- Proof of Work (PoW): In PoW, miners compete to solve cryptographic puzzles to validate transactions and create new blocks. This type of consensus mechanism requires computational power, making it a less environmentally friendly method. The concept behind PoW is that miners must financially invest and commit resources to approve transactions, so they are incentivized to be “good actors.”
- Proof of Stake (PoS): In PoS, validators hold a stake in the network and are chosen to validate transactions based on the amount of the stake they hold. Seen as a more environmentally friendly option, it is very expensive to become a full validator and earn rewards.
- Delegated Proof of Stake (DPoS): DPoS is a variant of proof of stake where the network selects a limited number of validators to validate transactions. This variation reduces the computational resources required to secure the network. In many ways, a DPoS system is seen as a more democratic means of selecting approvers and, in some instances, might offer better scalability.
Distributed Ledgers vs. Blockchain
There are several key factors that distinguish blockchain from distributed ledgers. In general, blockchain is a specific type of DLT. DLTs may take various forms, while a blockchain uses one specific infrastructure that uses a linear system of blocks to record and verify information.
Blockchains often leverage a proof of work or proof of stake consensus mechanism, whereas a DLT has a much broader range of mechanisms available. In addition, DLTs are often more broadly used across industries as they can be leveraged for broader problems. Blockchain has historically been most associated with the financial sector as a means of recording a payment system. The security behind either may also vary, with blockchain having a very defined set of criteria within the DLT realm.
Blockchain
-
Data is stored in chained files called “blocks”
-
Always encrypted
-
Generally public and permissionless, but some are permissioned
-
Always immutable
What Is Another Word For Distributed Ledger?
You might hear a distributed ledger called a share ledger.
Are DLT and Blockchain the Same?
All blockchains are distributed ledgers (DLs), but the opposite is not true—blockchains are derived from DLs.
What Is the Difference Between a Distibuted Ledger and a Centralized Ledger?
A centralized ledger is a database stored in a centralized location. It could be hosted by an individual, group, or organization that maintains it. A distributed ledger is a database where a copy is distributed, shared, and automatically synchronized.
What Is Meaning of DLT?
Distributed ledger technology is the concept of using modern networking systems, hardware, and programming to distribute copies of a database to multiple nodes that synchronize it to maintain it.
The Bottom Line
Distributed ledger technology uses databases stored on separate, connected devices in a network to ensure data accuracy and security. Blockchains evolved from distributed ledgers to address growing concerns that too many third parties are involved in too many transactions.
Distributed ledger technology is becoming necessary in modern businesses and enterprises that need to ensure accuracy in financial reporting, manage supply chains, prevent fraud, and identify inefficiencies. It has many more use cases in time-consuming and costly business activities.
News
An enhanced consensus algorithm for blockchain
The introduction of the link and reputation evaluation concepts aims to improve the stability and security of the consensus mechanism, decrease the likelihood of malicious nodes joining the consensus, and increase the reliability of the selected consensus nodes.
The link model structure based on joint action
Through the LINK between nodes, all the LINK nodes engage in consistent activities during the operation of the consensus mechanism. The reputation evaluation mechanism evaluates the trustworthiness of nodes based on their historical activity status throughout the entire blockchain. The essence of LINK is to drive inactive nodes to participate in system activities through active nodes. During the stage of selecting leader nodes, nodes are selected through self-recommendation, and the reputation evaluation of candidate nodes and their LINK nodes must be qualified. The top 5 nodes of the total nodes are elected as leader nodes through voting, and the nodes in their LINK status are candidate nodes. In the event that the leader node goes down, the responsibility of the leader node is transferred to the nodes in its LINK through the view-change. The LINK connection algorithm used in this study is shown in Table 2, where LINKm is the linked group and LINKP is the percentage of linked nodes.
Table 2 LINK connection algorithm.
Node type
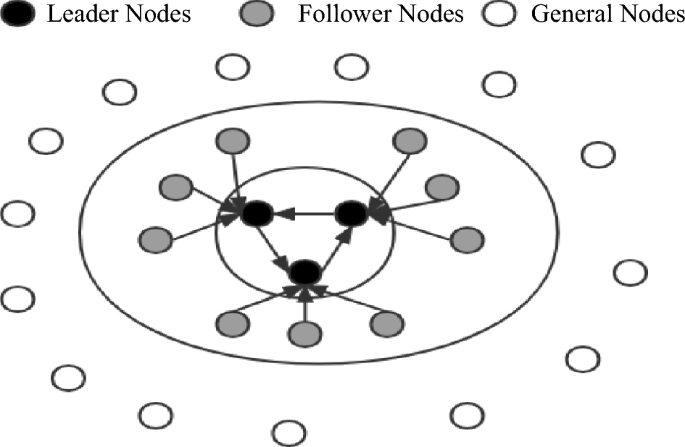
This paper presents a classification of nodes in a blockchain system based on their functionalities. The nodes are divided into three categories: leader nodes (LNs), follower nodes (FNs), and general nodes (Ns). The leader nodes (LNs) are responsible for producing blocks and are elected through voting by general nodes. The follower nodes (FNs) are nodes that are linked to leader nodes (LNs) through the LINK mechanism and are responsible for validating blocks. General nodes (N) have the ability to broadcast and disseminate information, participate in elections, and vote. The primary purpose of the LINK mechanism is to act in combination. When nodes are in the LINK, there is a distinction between the master and slave nodes, and there is a limit to the number of nodes in the LINK group (NP = {n1, nf1, nf2 ……,nfn}). As the largest proportion of nodes in the system, general nodes (N) have the right to vote and be elected. In contrast, leader nodes (LNs) and follower nodes (FNs) do not possess this right. This rule reduces the likelihood of a single node dominating the block. When the system needs to change its fundamental settings due to an increase in the number of nodes or transaction volume, a specific number of current leader nodes and candidate nodes need to vote for a reset. Subsequently, general nodes need to vote to confirm this. When both confirmations are successful, the new basic settings are used in the next cycle of the system process. This dual confirmation setting ensures the fairness of the blockchain to a considerable extent. It also ensures that the majority holds the ultimate decision-making power, thereby avoiding the phenomenon of a small number of nodes completely controlling the system.
After the completion of a governance cycle, the blockchain network will conduct a fresh election for the leader and follower nodes. As only general nodes possess the privilege to participate in the election process, the previous consortium of leader and follower nodes will lose their authorization. In the current cycle, they will solely retain broadcasting and receiving permissions for block information, while their corresponding incentives will also decrease. A diagram illustrating the node status can be found in Fig. 1.
Election method
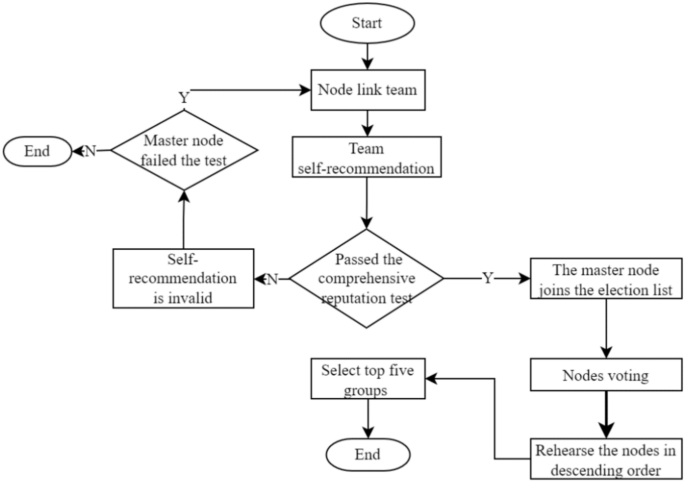
The election method adopts the node self-nomination mode. If a node wants to participate in an election, it must form a node group with one master and three slaves. One master node group and three slave node groups are inferred based on experience in this paper; these groups can balance efficiency and security and are suitable for other project collaborations. The successfully elected node joins the leader node set, and its slave nodes enter the follower node set. Considering the network situation, the maximum threshold for producing a block is set to 1 s. If the block fails to be successfully generated within the specified time, it is regarded as a disconnected state, and its reputation score is deducted. The node is skipped, and in severe cases, a view transformation is performed, switching from the master node to the slave node and inheriting its leader’s rights in the next round of block generation. Although the nodes that become leaders are high-reputation nodes, they still have the possibility of misconduct. If a node engages in misconduct, its activity will be immediately stopped, its comprehensive reputation score will be lowered, it will be disqualified from participating in the next election, and its equity will be reduced by 30%. The election process is shown in Fig. 2.
Incentives and penalties
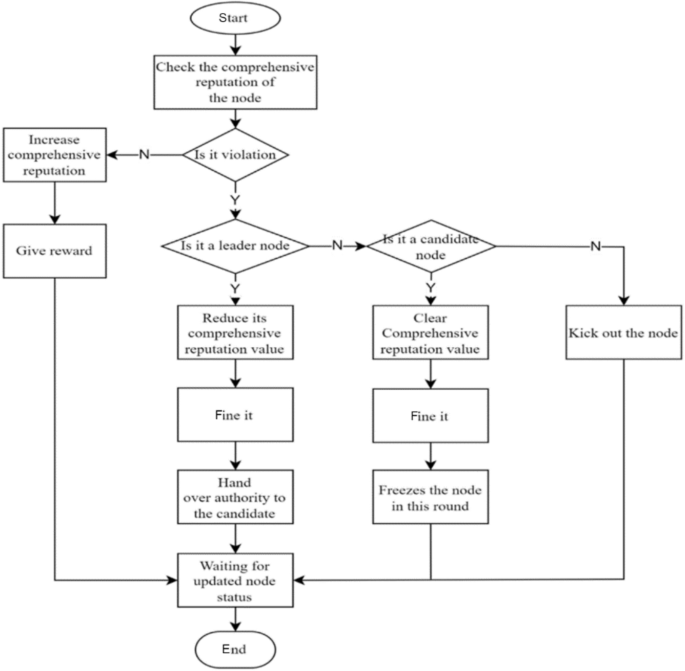
To balance the rewards between leader nodes and ordinary nodes and prevent a large income gap, two incentive/penalty methods will be employed. First, as the number of network nodes and transaction volume increase, more active nodes with significant stakes emerge. After a prolonged period of running the blockchain, there will inevitably be significant class distinctions, and ordinary nodes will not be able to win in the election without special circumstances. To address this issue, this paper proposes that rewards be reduced for nodes with stakes exceeding a certain threshold, with the reduction rate increasing linearly until it reaches zero. Second, in the event that a leader or follower node violates the consensus process, such as by producing a block out of order or being unresponsive for an extended period, penalties will be imposed. The violation handling process is illustrated in Fig. 3.
Violation handling process.
Comprehensive reputation evaluation and election mechanism based on historical transactions
This paper reveals that the core of the DPoS consensus mechanism is the election process. If a blockchain is to run stably for a long time, it is essential to consider a reasonable election method. This paper proposes a comprehensive reputation evaluation election mechanism based on historical records. The mechanism considers the performance indicators of nodes in three dimensions: production rate, tokens, and validity. Additionally, their historical records are considered, particularly whether or not the nodes have engaged in malicious behavior. For example, nodes that have ever been malicious will receive low scores during the election process unless their overall quality is exceptionally high and they have considerable support from other nodes. Only in this case can such a node be eligible for election or become a leader node. The comprehensive reputation score is the node’s self-evaluation score, and the committee size does not affect the computational complexity.
Moreover, the comprehensive reputation evaluation proposed in this paper not only is a threshold required for node election but also converts the evaluation into corresponding votes based on the number of voters. Therefore, the election is related not only to the benefits obtained by the node but also to its comprehensive evaluation and the number of voters. If two nodes receive the same vote, the node with a higher comprehensive reputation is given priority in the ranking. For example, in an election where node A and node B each receive 1000 votes, node A’s number of stake votes is 800, its comprehensive reputation score is 50, and only four nodes vote for it. Node B’s number of stake votes is 600, its comprehensive reputation score is 80, and it receives votes from five nodes. In this situation, if only one leader node position remains, B will be selected as the leader node. Displayed in descending order of priority as comprehensive credit rating, number of voters, and stake votes, this approach aims to solve the problem of node misconduct at its root by democratizing the process and subjecting leader nodes to constraints, thereby safeguarding the fundamental interests of the vast majority of nodes.
Comprehensive reputation evaluation
This paper argues that the election process of the DPoS consensus mechanism is too simplistic, as it considers only the number of election votes that a node receives. This approach fails to comprehensively reflect the node’s actual capabilities and does not consider the voters’ election preferences. As a result, nodes with a significant stake often win and become leader nodes. To address this issue, the comprehensive reputation evaluation score is normalized considering various attributes of the nodes. The scoring results are shown in Table 3.
Table 3 Comprehensive reputation evaluation.
Since some of the evaluation indicators in Table 3 are continuous while others are discrete, different normalization methods need to be employed to obtain corresponding scores for different indicators. The continuous indicators include the number of transactions/people, wealth balance, network latency, network jitter, and network bandwidth, while the discrete indicators include the number of violations, the number of successful elections, and the number of votes. The value range of the indicator “number of transactions/people” is (0,1), and the value range of the other indicators is (0, + ∞). The equation for calculating the “number of transactions/people” is set as shown in Eq. (1).
$$A_{1} = \left\{ {\begin{array}{*{20}l} {0,} \hfill & {{\text{G}} = 0} \hfill \\ {\frac{{\text{N}}}{{\text{G}}}*10,} \hfill & {{\text{G}} > 0} \hfill \\ \end{array} } \right.$$
(1)
where N represents the number of transactional nodes and G represents the number of transactions. It reflects the degree of connection between the node and other nodes. Generally, nodes that transact with many others are safer than those with a large number of transactions with only a few nodes. The limit value of each item, denoted by x, is determined based on the situation and falls within the specified range, as shown in Eq. (2). The wealth balance and network bandwidth indicators use the same function to set their respective values.
$${A}_{i}=20*\left(\frac{1}{1+{e}^{-{a}_{i}x}}-0.5\right)$$
(2)
where x indicates the value of this item and expresses the limit value.
In Eq. (3), x represents the limited value of this indicator. The lower the network latency and network jitter are, the higher the score will be.
The last indicators, which are the number of violations, the number of elections, and the number of votes, are discrete values and are assigned different scores according to their respective ranges. The scores corresponding to each count are shown in Table 4.
$$A_{3} = \left\{ {\begin{array}{*{20}l} {10*\cos \frac{\pi }{200}x,} \hfill & {0 \le x \le 100} \hfill \\ {0,} \hfill & {x > 100} \hfill \\ \end{array} } \right.$$
(3)
Table 4 Score conversion.
The reputation evaluation mechanism proposed in this paper comprehensively considers three aspects of nodes, wealth level, node performance, and stability, to calculate their scores. Moreover, the scores obtain the present data based on historical records. Each node is set as an M × N dimensional matrix, where M represents M times the reputation evaluation score and N represents N dimensions of reputation evaluation (M < = N), as shown in Eq. (4).
$${\text{N}} = \left( {\begin{array}{*{20}c} {a_{11} } & \cdots & {a_{1n} } \\ \vdots & \ddots & \vdots \\ {a_{m1} } & \cdots & {a_{mn} } \\ \end{array} } \right)$$
(4)
The comprehensive reputation rating is a combined concept related to three dimensions. The rating is set after rating each aspect of the node. The weight w and the matrix l are not fixed. They are also transformed into matrix states as the position of the node in the system changes. The result of the rating is set as the output using Eq. (5).
$$\text{T}=\text{lN}{w}^{T}=\left({l}_{1}\dots {\text{l}}_{\text{m}}\right)\left(\begin{array}{ccc}{a}_{11}& \cdots & {a}_{1n}\\ \vdots & \ddots & \vdots \\ {a}_{m1}& \cdots & {a}_{mn}\end{array}\right){\left({w}_{1}\dots {w}_{n}\right)}^{T}$$
(5)
Here, T represents the comprehensive reputation score, and l and w represent the correlation coefficient. Because l is a matrix of order 1*M, M is the number of times in historical records, and M < = N is set, the number of dimensions of l is uncertain. Set the term l above to add up to 1, which is l1 + l2 + …… + ln = 1; w is also a one-dimensional matrix whose dimension is N*1, and its purpose is to act as a weight; within a certain period of time, w is a fixed matrix, and w will not change until the system changes the basic settings.
Assume that a node conducts its first comprehensive reputation rating, with no previous transaction volume, violations, elections or vote. The initial wealth of the node is 10, the latency is 50 ms, the jitter is 100 ms, and the network bandwidth is 100 M. According to the equation, the node’s comprehensive reputation rating is 41.55. This score is relatively good at the beginning and gradually increases as the patient participates in system activities continuously.
Voting calculation method
To ensure the security and stability of the blockchain system, this paper combines the comprehensive reputation score with voting and randomly sorts the blocks, as shown in Eqs. (3–6).
$$Z=\sum_{i=1}^{n}{X}_{i}+nT$$
(6)
where Z represents the final election score, Xi represents the voting rights earned by the node, n is the number of nodes that vote for this node, and T is the comprehensive reputation score.
The voting process is divided into stake votes and reputation votes. The more reputation scores and voters there are, the more total votes that are obtained. In the early stages of blockchain operation, nodes have relatively few stakes, so the impact of reputation votes is greater than that of equity votes. This is aimed at selecting the most suitable node as the leader node in the early stage. As an operation progresses, the role of equity votes becomes increasingly important, and corresponding mechanisms need to be established to regulate it. The election vote algorithm used in this paper is shown in Table 5.
Table 5 Election vote counting algorithm.
This paper argues that the election process utilized by the original DPoS consensus mechanism is overly simplistic, as it relies solely on the vote count to select the node that will oversee the entire blockchain. This approach cannot ensure the security and stability of the voting process, and if a malicious node behaves improperly during an election, it can pose a significant threat to the stability and security of the system as well as the safety of other nodes’ assets. Therefore, this paper proposes a different approach to the election process of the DPoS consensus mechanism by increasing the complexity of the process. We set up a threshold and optimized the vote-counting process to enhance the security and stability of the election. The specific performance of the proposed method was verified through experiments.
The election cycle in this paper can be customized, but it requires the agreement of the blockchain committee and general nodes. The election cycle includes four steps: node self-recommendation, calculating the comprehensive reputation score, voting, and replacing the new leader. Election is conducted only among general nodes without affecting the production or verification processes of leader nodes or follower nodes. Nodes start voting for preferred nodes. If they have no preference, they can use the LINK mechanism to collaborate with other nodes and gain additional rewards.
View changes
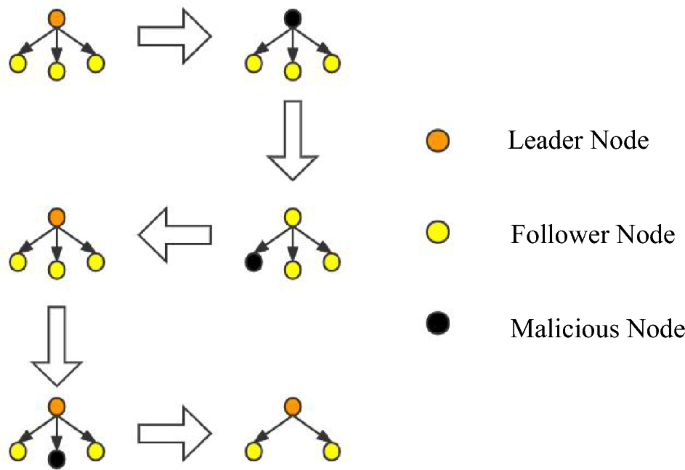
During the consensus process, conducting a large number of updates is not in line with the system’s interests, as the leader node (LN) and follower node (FN) on each node have already been established. Therefore, it is crucial to handle problematic nodes accurately when issues arise with either the LN or FN. For instance, when a node fails to perform its duties for an extended period or frequently fails to produce or verify blocks within the specified time range due to latency, the system will precisely handle them. For leader nodes, if they engage in malicious behavior such as producing blocks out of order, the behavior is recorded, and their identity as a leader node is downgraded to a follower node. The follower node inherits the leader node’s position, and the nature of their work is transformed as they swap their responsibilities of producing and verifying blocks with their original work. This type of behavior will not significantly affect the operation of the blockchain system. Instead of waiting until the end of the current committee round to punish malicious nodes, dynamic punishment is imposed on the nodes that affect the operation of the blockchain system to maintain system security. The view change operation is illustrated in Fig. 4.
In traditional PBFT, view changes are performed according to the view change protocol by changing the view number V to the next view number V + 1. During this process, nodes only receive view change messages and no other messages from other nodes. In this paper, the leader node group (LN) and follower node group (FN) are selected through an election of the LINK group. The node with LINKi[0] is added to the LN leader node group, while the other three LINK groups’ follower nodes join the FN follower node group since it is a configuration pattern of one master and three slaves. The view change in this paper requires only rearranging the node order within the LINK group to easily remove malicious nodes. Afterward, the change is broadcast to other committee nodes, and during the view transition, the LINK group does not receive block production or verification commands from the committee for stability reasons until the transition is completed.
News
The Hype Around Blockchain Mortgage Has Died Down, But This CEO Still Believes

LiquidFi Founder Ian Ferreira Sees Huge Potential in Blockchain Despite Hype around technology is dead.
“Blockchain technology has been a buzzword for a long time, and it shouldn’t be,” Ferriera said. “It should be a technology that lives in the background, but it makes everything much more efficient, much more transparent, and ultimately it saves costs for everyone. That’s the goal.”
Before founding his firm, Ferriera was a portfolio manager at a hedge fund, a job that ended up revealing “interesting intricacies” related to the mortgage industry.
Being a mortgage trader opened Ferriera’s eyes to a lot of the operational and infrastructure problems that needed to be solved in the mortgage-backed securities industry, he said. That later led to the birth of LiquidFi.
“The point of what we do is to get raw data attached to a resource [a loan] on a blockchain so that it’s provable. You reduce that trust problem because you have the data, you have the document associated with that data,” said the LiquidFi CEO.
Ferriera spoke with National Mortgage News about the value of blockchain technology, why blockchain hype has fizzled out, and why it shouldn’t.
News
New bill pushes Department of Veterans Affairs to examine how blockchain can improve its work

The Department of Veterans Affairs would have to evaluate how blockchain technology could be used to improve benefits and services offered to veterans, according to a legislative proposal introduced Tuesday.
The bill, sponsored by Rep. Nancy Mace, R-S.C., would direct the VA to “conduct a comprehensive study of the feasibility, potential benefits, and risks associated with using distributed ledger technology in various programs and services.”
Distributed ledger technology, including blockchain, is used to protect and track information by storing data across multiple computers and keeping a record of its use.
According to the text of the legislation, which Mace’s office shared exclusively with Nextgov/FCW ahead of its publication, blockchain “could significantly improve benefits allocation, insurance program management, and recordkeeping within the Department of Veterans Affairs.”
“We need to bring the federal government into the 21st century,” Mace said in a statement. “This bill will open the door to research on improving outdated systems that fail our veterans because we owe it to them to use every tool at our disposal to improve their lives.”
Within one year of the law taking effect, the Department of Veterans Affairs will be required to submit a report to the House and Senate Veterans Affairs committees detailing its findings, as well as the benefits and risks identified in using the technology.
The mandatory review is expected to include information on how the department’s use of blockchain could improve the way benefits decisions are administered, improve the management and security of veterans’ personal data, streamline the insurance claims process, and “increase transparency and accountability in service delivery.”
The Department of Veterans Affairs has been studying the potential benefits of using distributed ledger technology, with the department emission a request for information in November 2021 seeking input from contractors on how blockchain could be leveraged, in part, to streamline its supply chains and “secure data sharing between institutions.”
The VA’s National Institute of Artificial Intelligence has also valued the use of blockchain, with three of the use cases tested during the 2021 AI tech sprint focused on examining its capabilities.
Mace previously introduced a May bill that would direct Customs and Border Protection to create a public blockchain platform to store and share data collected at U.S. borders.
Lawmakers also proposed additional measures that would push the Department of Veterans Affairs to consider adopting other modernized technologies to improve veteran services.
Rep. David Valadao, R-Calif., introduced legislation in June that would have directed the department to report to lawmakers on how it plans to expand the use of “certain automation tools” to process veterans’ claims. The House of Representatives Subcommittee on Disability Assistance and Memorial Affairs gave a favorable hearing on the congressman’s bill during a Markup of July 23.
News
California DMV Uses Blockchain to Fight Auto Title Fraud

TDR’s Three Takeaways: California DMV Uses Blockchain to Fight Fraud
- California DMV uses blockchain technology to manage 42 million auto titles.
- The initiative aims to improve safety and reduce car title fraud.
- The immutable nature of blockchain ensures accurate and tamper-proof records.
The California Department of Motor Vehicles (DMV) is implementing blockchain technology to manage and secure 42 million auto titles. This innovative move aims to address and reduce the persistent problem of auto title fraud, a problem that costs consumers and the industry millions of dollars each year. By moving to a blockchain-based system, the DMV is taking advantage of the technology’s key feature: immutability.
Blockchain, a decentralized ledger technology, ensures that once a car title is registered, it cannot be altered or tampered with. This creates a highly secure and transparent system, significantly reducing the risk of fraudulent activity. Every transaction and update made to a car title is permanently recorded on the blockchain, providing a complete and immutable history of the vehicle’s ownership and status.
As first reported by Reuters, the DMV’s adoption of blockchain isn’t just about preventing fraud. It’s also aimed at streamlining the auto title process, making it more efficient and intuitive. Traditional auto title processing involves a lot of paperwork and manual verification, which can be time-consuming and prone to human error. Blockchain technology automates and digitizes this process, reducing the need for physical documents and minimizing the chances of errors.
Additionally, blockchain enables faster verification and transfer of car titles. For example, when a car is sold, the transfer of ownership can be done almost instantly on the blockchain, compared to days or even weeks in the conventional system. This speed and efficiency can benefit both the DMV and the vehicle owners.
The California DMV’s move is part of a broader trend of government agencies exploring blockchain technology to improve their services. By adopting this technology, the DMV is setting a precedent for other states and industries to follow, showcasing blockchain’s potential to improve safety and efficiency in public services.
-
 Ethereum11 months ago
Ethereum11 months agoEthereum Posts First Consecutive Monthly Losses Since August 2023 on New ETFs
-

 Regulation11 months ago
Regulation11 months agoCryptocurrency Regulation in Slovenia 2024
-

 News11 months ago
News11 months agoNew bill pushes Department of Veterans Affairs to examine how blockchain can improve its work
-

 Regulation11 months ago
Regulation11 months agoThink You Own Your Crypto? New UK Law Would Ensure It – DL News
-

 Regulation11 months ago
Regulation11 months agoA Blank Slate for Cryptocurrencies: Kamala Harris’ Regulatory Opportunity
-

 Regulation11 months ago
Regulation11 months agoUpbit, Coinone, Bithumb Face New Fees Under South Korea’s Cryptocurrency Law
-

 Regulation11 months ago
Regulation11 months agoBahamas Passes Cryptocurrency Bill Designed to Prevent FTX, Terra Disasters
-

 Regulation11 months ago
Regulation11 months agoIndia to Follow G20 Policy for Cryptocurrency Regulation: MoS Finance
-

 Ethereum1 year ago
Ethereum1 year agoComment deux frères auraient dérobé 25 millions de dollars lors d’un braquage d’Ethereum de 12 secondes • The Register
-

 Videos1 year ago
Videos1 year agoNexus Chain – Ethereum L2 with the GREATEST Potential?
-

 News11 months ago
News11 months agoEU supports 15 startups to fight online disinformation with blockchain
-

 News1 year ago
News1 year agoSolana ranks the fastest blockchain in the world, surpassing Ethereum, Polygon ⋆ ZyCrypto