News
What Is Cryptocurrency| Simplilearn
![What is Blockchain Technology? How Does Blockchain Work? [Updated]](https://chainfeed.info/wp-content/uploads/2024/07/1720422010_What-is-Blockchain-Technology-How-Does-Blockchain-Work-Updated.png)
Cryptocurrencies have become increasingly popular over the past several years – as of 2018, there were more than 1,600 of them! And the number is constantly growing. With that has come to an increase in demand for developers of the blockchain (the underlying technology of cryptocurrencies such as bitcoin). The salaries blockchain developers earn show how much they are valued: According to Indeed, the average salary of a full-stack developer is more than $112,000. There’s even a dedicated website for cryptocurrency jobs.
Whether you’re interested in a career as a blockchain developer or you just want to keep up with the latest trends in tech, Simplilearn’s Cryptocurrency Explained video explains what cryptocurrency is and why it’s important will get you off to a good start. Here we’ll recap what’s covered in the video.
Basics to Advanced – Learn It All!
Caltech PGP Full Stack DevelopmentExplore Program
A Brief History of Cryptocurrency
In the caveman era, people used the barter system, in which goods and services are exchanged among two or more people. For instance, someone might exchange seven apples for seven oranges. The barter system fell out of popular use because it had some glaring flaws:
- People’s requirements have to coincide—if you have something to trade, someone else has to want it, and you have to want what the other person is offering.
- There’s no common measure of value—you have to decide how many of your items you are willing to trade for other items, and not all items can be divided. For example, you cannot divide a live animal into smaller units.
- The goods cannot be transported easily, unlike our modern currency, which fits in a wallet or is stored on a mobile phone.
After people realized the barter system didn’t work very well, the currency went through a few iterations: In 110 B.C., an official currency was minted; in A.D. 1250, gold-plated florins were introduced and used across Europe; and from 1600 to 1900, the paper currency gained widespread popularity and ended up being used around the world. This is how modern currency as we know it came into existence.
Modern currency includes paper currency, coins, credit cards, and digital wallets—for example, Apple Pay, Amazon Pay, Paytm, PayPal, and so on. All of it is controlled by banks and governments, meaning that there is a centralized regulatory authority that limits how paper currency and credit cards work.
Traditional Currencies vs. Cryptocurrencies
Imagine a scenario in which you want to repay a friend who bought you lunch, by sending money online to his or her account. There are several ways in which this could go wrong, including:
- The financial institution could have a technical issue, such as its systems are down or the machines aren’t working properly.
- Your or your friend’s account could have been hacked—for example, there could be a denial-of-service attack or identity theft.
- The transfer limits for your or your friend’s account could have been exceeded.
There is a central point of failure: the bank.
This is why the future of currency lies with cryptocurrency. Now imagine a similar transaction between two people using the bitcoin app. A notification appears asking whether the person is sure he or she is ready to transfer bitcoins. If yes, processing takes place: The system authenticates the user’s identity, checks whether the user has the required balance to make that transaction, and so on. After that’s done, the payment is transferred and the money lands in the receiver’s account. All of this happens in a matter of minutes.
Cryptocurrency, then, removes all the problems of modern banking: There are no limits to the funds you can transfer, your accounts cannot be hacked, and there is no central point of failure. As mentioned above, as of 2018 there are more than 1,600 cryptocurrencies available; some popular ones are Bitcoin, Litecoin, Ethereum, and Zcash. And a new cryptocurrency crops up every single day. Considering how much growth they’re experiencing at the moment, there’s a good chance that there are plenty more to come!
Moving forward, let us discuss what is cryptocurrency.
What is Cryptocurrency?
A cryptocurrency is a coded string of data representing a currency unit. Peer-to-peer networks called blockchains monitor and organize cryptocurrency transactions, such as buying, selling, and transferring, and also serve as secure ledgers of transactions. By utilizing encryption technology, cryptocurrencies can serve as both a currency and an accounting system.
A cryptocurrency is a digital or virtual currency that is meant to be a medium of exchange. It is quite similar to real-world currency, except it does not have any physical embodiment, and it uses cryptography to work.
Because cryptocurrencies operate independently and in a decentralized manner, without a bank or a central authority, new units can be added only after certain conditions are met. For example, with Bitcoin, only after a block has been added to the blockchain will the miner be rewarded with bitcoins, and this is the only way new bitcoins can be generated. The limit for bitcoins is 21 million; after this, no more bitcoins will be produced.
In the evolving landscape of finance and technology, the role of cybersecurity in the realm of cryptocurrency is paramount. A Cyber security BootCamp provides an ideal platform for individuals to delve into the intricacies of securing digital assets and transactions within the cryptocurrency domain. By gaining expertise in cryptographic principles, blockchain security, and risk management, participants are better equipped to address the unique challenges posed by digital currencies.
How Does Cryptocurrency Work?
Cryptocurrency is a digital or virtual currency that uses cryptography for security. A cryptocurrency is difficult to counterfeit because of this security feature. Cryptocurrencies are decentralized and not subject to government or financial institution control.
- And the decentralized control of each cryptocurrency works through distributed ledger technology, typically a blockchain, that serves as a public financial transaction database.
- The most famous cryptocurrency is Bitcoin, which was created in 2009.
- Cryptocurrencies are designed through mining, which uses computing power to solve complex math problems that verify transactions on the blockchain, the public ledger of all cryptocurrency transactions. And miners are rewarded with cryptocurrency for their efforts.
Cryptocurrency trading is speculative and complex, and it involves significant risks. Prices can fluctuate on any given day. Given the price volatility, cryptocurrency is only suitable for some investors. Therefore, cryptocurrency should be considered a high-risk investment. Before investing, understand the risks involved and consult a financial advisor.
Basics to Advanced – Learn It All!
Caltech PGP Full Stack DevelopmentExplore Program![]()
Benefits of Cryptocurrency
With cryptocurrency, the transaction cost is low to nothing at all—unlike, for example, the fee for transferring money from a digital wallet to a bank account. You can make transactions at any time of the day or night, and there are no limits on purchases and withdrawals. And anyone is free to use cryptocurrency, unlike setting up a bank account, which requires documentation and other paperwork.
International cryptocurrency transactions are faster than wire transfers too. Wire transfers take about half a day for the money to be moved from one place to another. With cryptocurrencies, transactions take only a matter of minutes or even seconds.

How to Buy Cryptocurrency?
Cryptocurrencies are digital or virtual tokens that use cryptography to secure their transactions and control the creation of new units. And cryptocurrencies are often bought with “fiat” or traditional currency like US dollars or euros. However, they can also be bought with cryptocurrencies like Bitcoin or Ethereum. First, you must set up a digital wallet to store your coins to buy cryptocurrency. You can then buy coins on a cryptocurrency exchange using your fiat currency or another cryptocurrency.
There are a few different ways to buy cryptocurrency.
- You can use an online cryptocurrency exchange such as Coinbase, Bitstamp, or Kraken to purchase cryptocurrency with a credit/debit card, bank transfer, or other payment methods.
- You can use a peer-to-peer exchange such as LocalBitcoins or Bisq to purchase cryptocurrency directly from other users.
- You can trade cryptocurrency for other types of assets, such as stocks, through cryptocurrency trading platforms.
How to Store Cryptocurrency?
Storing cryptocurrency securely is an integral part of investing in cryptocurrencies. Cryptocurrency can be stored in several ways, but the most common is through a digital wallet. A digital wallet can be software-based, web-based, or hardware-based.
- Software-based wallets are installed on a computer or mobile device, while web-based wallets are accessed through a web browser.
- Hardware-based wallets are physical devices that store cryptocurrency offline.
Digital wallets are used to store, send, and receive cryptocurrency. They are generally more secure than other wallets and not subject to hacking or malware. However, digital wallets can be recovered or stolen if adequately protected.
It is also essential to use strong passwords and two-factor authentication to protect the wallet. Additionally, using an address generated through a secure random number generator can help protect against address reuse and other security risks. And it would be best to keep your private key private, which can access your cryptocurrency.
What Can You Buy with Cryptocurrency?
You can buy various items with cryptocurrency, including digital assets such as domain names, gift cards, and software. You can also purchase physical objects such as electronics, furniture, artwork, and clothing. Additionally, some online retailers and physical stores accept cryptocurrency as payment. In addition, cryptocurrency can also help to invest in various businesses and projects. For example, you could use cryptocurrency to invest in a new start-up or to help fund a new product or service.
Basics to Advanced – Learn It All!
Caltech PGP Full Stack DevelopmentExplore Program![]()
What is Cryptography?
Cryptography is a method of using encryption and decryption to secure communication in the presence of third parties with ill intent—that is, third parties who want to steal your data or eavesdrop on your conversation. Cryptography uses computational algorithms such as SHA-256, which is the hashing algorithm that Bitcoin uses; a public key, which is like a digital identity of the user shared with everyone; and a private key, which is a digital signature of the user that is kept hidden.
Cryptography in Bitcoin Transactions
In a normal bitcoin transaction, first, there are the transaction details: whom you want to send the bitcoins to and how many bitcoins you want to send. Then the information is passed through a hashing algorithm. Bitcoin uses the SHA-256 algorithm. The output is then passed through a signature algorithm with the user’s private key, used to uniquely identify the user. The digitally signed output is then distributed across the network for other users to verify. This is done by using the sender’s public key.
The users who check the transaction to see whether it’s valid or not are known as miners. After this is done, the transaction and several others are added to the blockchain, where the details cannot be changed. The SHA-256 algorithm looks something like in the image below.
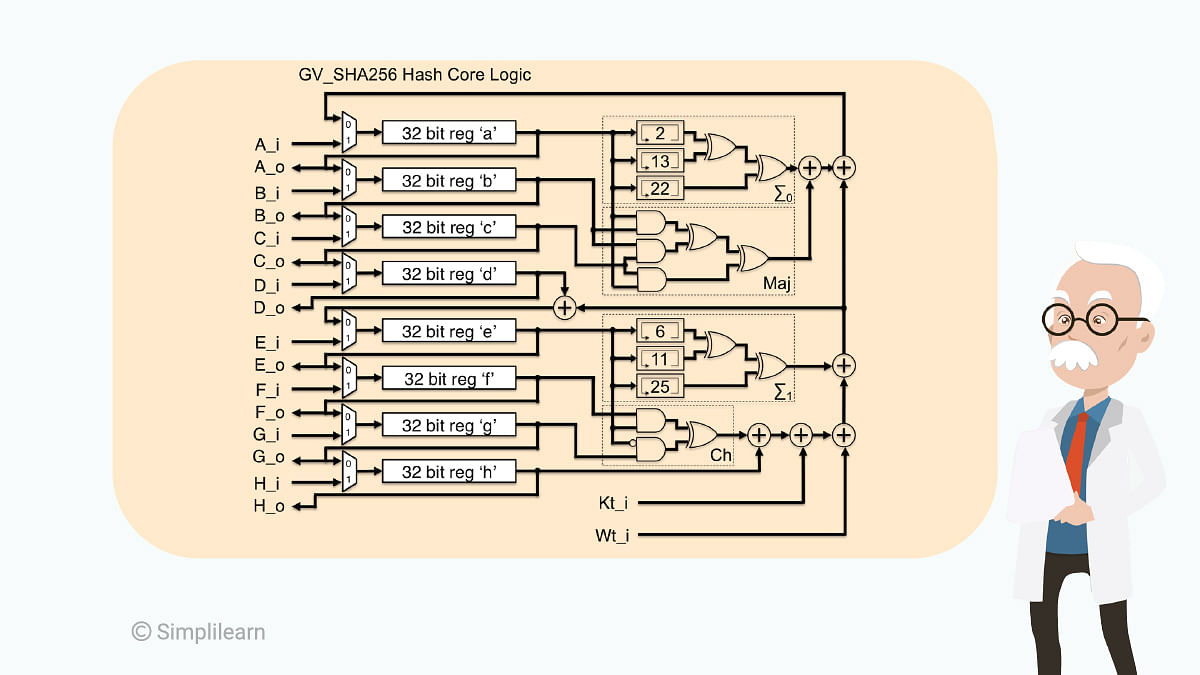
You can see how complicated it is, meaning it’s safe to say that the encryption is very difficult to hack.
Bitcoin vs. Ethereum
You now know that Bitcoin is a digital currency that is decentralized and works on the blockchain technology and that it uses a peer-to-peer network to perform transactions. Ether is another popular digital currency, and it’s accepted in the Ethereum network. The Ethereum network uses blockchain technology to create an open-source platform for building and deploying decentralized applications.
Similarities
Bitcoin and ether are the biggest and most valuable cryptocurrencies right now. Both of them use blockchain technology, in which transactions are added to a container called a block, and a chain of blocks is created in which data cannot be altered. For both, the currency is mined using a method called proof of work, involving a mathematical puzzle that needs to be solved before a block can be added to the blockchain. Finally, both bitcoin and ether are widely used around the world.
Differences
Bitcoin is used to send money to someone. The way it works is very similar to the way real-life currency works. Ether is used as a currency within the Ethereum network, although it can be used for real-life transactions as well. Bitcoin transactions are done manually, which means you have to personally perform these transactions when you want them done. With ether, you have the option to make transactions manual or automatic—they are programmable, which means the transactions take place when certain conditions have been met. As for timing, it takes about 10 minutes to perform a bitcoin transaction—this is the time it takes for a block to be added to the blockchain. With ether, it takes about 20 seconds to do a transaction.
There is a limit to how many bitcoins can exist: 21 million. This number is supposed to be reached by the year 2140. Ether is expected to be around for a while and is not to exceed 100 million units. Bitcoin is used for transactions involving goods and services, and ether uses blockchain technology to create a ledger to trigger a transaction when a certain condition is met. Finally, Bitcoin uses the SHA-256 algorithm, and Ethereum uses the ethash algorithm.
As of May 2020, 1 bitcoin equals $8741.81 dollars, and 1 ether equals $190.00.
Cryptocurrency Fraud and Cryptocurrency Scams
Cryptocurrency fraud and scams are becoming increasingly common as the popularity of cryptocurrencies grows. Cryptocurrency fraud is any form of deceptive or criminal activity or deliberate manipulation of the value of digital currencies, whether through hacking, fraud, market manipulation, or other malicious activities.
On the other hand, cryptocurrency scams involve any fraudulent activity or schemes related to the acquisition, trading, or use of virtual currencies. These scams are typically perpetrated through online marketplaces, social media platforms, or other channels. Such scams include fraudulent online exchanges, pump-and-dump schemes, and pyramid schemes.
Scammers can defraud investors in a few different ways, including
- Ponzi schemes: In a Ponzi scheme, investors are promised unrealistic returns and paid back with money from new investors. Eventually, the scheme collapses when there need to be more new investors to keep it going.
- Pyramid schemes: Similar to a Ponzi scheme, investors are promised unrealistic returns in a pyramid scheme. However, instead of being paid back with money from new investors, they are paid back with their own or from other investors in the scheme.
- Fake ICOs: An ICO, or initial coin offering, is a way for a company to raise money by selling digital tokens. Unfortunately, some scammers create fake ICOs to steal investors’ money.
- Hacking: Hacking is a major issue in the cryptocurrency world. Hackers can steal money from exchanges, wallets, and individual investors.
These are just a few of the ways that scammers can defraud investors. Therefore, it’s essential to know the risks before investing in cryptocurrencies.
Is Cryptocurrency Safe?
Cryptocurrency is generally considered safe, although your account’s security depends on the measures you take to protect it. For example, using strong passwords, enabling two-factor authentication, and never sharing your private keys or passwords with anyone is important.
4 Tips to Invest in Cryptocurrency Safely
- Research and Understand the Market: Before investing in cryptocurrency, it is crucial to research and understand the market. Understanding the technology, benefits, and risks associated with investing in cryptocurrency.
- Use Reputable Exchange Platforms: Investors should only use reputable exchanges to buy and sell cryptocurrency. Reputable exchange platforms have built-in security measures that protect investors from theft and fraud.
- Store Cryptocurrency Securely: It is vital to store cryptocurrency securely after purchasing cryptocurrency. Investing in a secure wallet is one of the best ways to protect cryptocurrencies from theft and fraud.
- Diversify Investments: Diversifying investments can help to manage the risks associated with investing in cryptocurrency. For example, buy different types of cryptocurrency to spread out the threat.
Basics to Advanced – Learn It All!
Caltech PGP Full Stack DevelopmentExplore Program![]()
The Future of Cryptocurrency
The world is clearly divided when it comes to cryptocurrencies. On one side are supporters such as Bill Gates, Al Gore and Richard Branson, who say that cryptocurrencies are better than regular currencies. On the other side are people such as Warren Buffet, Paul Krugman, and Robert Shiller, who are against it. Krugman and Shiller, who are both Nobel Prize winners in the field of economics, call it a Ponzi scheme and a means for criminal activities.
In the future, there’s going to be a conflict between regulation and anonymity. Since several cryptocurrencies have been linked with terrorist attacks, governments would want to regulate how cryptocurrencies work. On the other hand, the main emphasis of cryptocurrencies is to ensure that users remain anonymous.
Futurists believe that by the year 2030, cryptocurrencies will occupy 25 percent of national currencies, which means a significant chunk of the world would start believing in cryptocurrency as a mode of transaction. It’s going to be increasingly accepted by merchants and customers, and it will continue to have a volatile nature, which means prices will continue to fluctuate, as they have been doing for the past few years.
That wraps up our cryptocurrency tutorial. If you’d like to learn more about blockchain (the underlying technology of cryptocurrencies such as bitcoin), check out Professional Certificate Program in Blockchain by IIT Kanpur.
If you have any questions in the article “what is cryptocurrency”, please ask your questions in the comment section below. Our experts will get back to you at the earliest.
FAQs
1. How do you buy Cryptocurrencies?
Bitcoin may be traded on exchanges, which provide investors with a safe and secure platform. The future has here with cryptocurrencies. To begin investing, you must first choose a reputable cryptocurrency exchange where you may buy, sell, and trade cryptocurrencies like Bitcoin, Ethereum, Tron, and others. Select a Broker or a Crypto Exchange. You must first select a broker or cryptocurrency exchange to purchase bitcoin. Then you must create and validate Your Account. Make a cash deposit to begin investing, and then place your cryptocurrency order. Choose a Storage Method.
2. What is the point of Cryptocurrency?
Anyone can send and receive money anywhere, using the peer-to-peer payment system. In the real world, cryptocurrency transactions are not carried around and exchanged as tangible money but as digital entries to an online database that identifies specific transactions. The benefits of cryptocurrencies include cheaper and quicker money transactions and decentralized systems that do not fail at a single point.
3. Can you generate Cryptocurrency?
Anyone may establish a cryptocurrency, but it takes time, money, and other resources, as well as extensive technical skills. The primary possibilities are creating your own blockchain, modifying an existing one, creating a coin on an existing one, or hiring a blockchain engineer. The cost of bitcoin production ranges from $10,000 to $30,000, depending on the chosen option.
4. What are the most popular Cryptocurrencies?
Consider Ravencoin, Ethereum, and Bitcoin to purchase today and retain forever. Due to their volatility, cryptocurrencies are best suited for those that can tolerate risk. For these investors, investing in the leading cryptocurrencies now, while the market is unreliable, may pay off in the long term. One of the biggest cryptocurrency exchanges in the world, Binance, has its own coin called BNB. Although Binance Coin was first designed as a token to pay for reduced transactions, it is now being used to make payments and buy a variety of goods and services.
5. Are Cryptocurrencies Securities?
On the Chicago Mercantile Exchange, the world’s largest and most complex financial market, crypto derivatives like Bitcoin futures are offered. According to the Securities and Exchange Commission (SEC), Ethereum and Bitcoin are not securities.
6. How do cryptocurrencies work?
A digital currency, or cryptocurrency, is an alternative payment method developed utilizing encryption methods. By utilizing encryption technology, cryptocurrencies may act as both a medium of exchange and a virtual accounting system. You need a cryptocurrency wallet in order to utilize cryptocurrencies. Blockchain networks power cryptocurrencies. A blockchain is simply a growing collection of digital blocks that serve as a ledger. The distributed ledger of a blockchain allows for the storage of data across several computers in a network. The nodes are the individual computers that validate and store the data.
7. How to invest in cryptocurrency?
Opt for the bitcoin exchange of your choice. Create an account with the bitcoin exchange after that. Spend fiat money to fill your account. Choose the cryptocurrency that you wish to purchase. Put up a purchase order for the cryptocurrency of your choice.
8. What are the key steps to buy cryptocurrency?
Step 1: Pick the best cryptocurrency exchange.
Step 2: Open a trading account and confirm your email. Connect your phone now.
Step 3: Verify your identification in step three. Fund Your Account next.
Step 4: Purchasing and Investing in Cryptocurrency.
Step 5: Store your cryptocurrency.
Step 6: Choose a strategy in the last step.
9. What is the minimum amount you can invest in cryptocurrencies?
You may buy or sell digital money for as low as $2.00 ($2 or €2) that is denominated in your home currency.
10. Can cryptocurrencies be used to make online purchases?
Definitely, despite the fact that cryptocurrencies are not a commonly utilized payment option, a number of businesses have started to accept them in return for their goods and services. Online purchases are increasingly being made using cryptocurrencies. According to Wagner, a number of merchants now accept Bitcoin. You may shop on Overstock.com to buy furniture for your home with cryptocurrency. You may even embark on a spending spree at Nordstrom, which also accepts Bitcoin from clients.
11. How many Cryptocurrencies are there?
There are already more than 12,000 cryptocurrencies, and the growth rate is simply astounding. Cryptocurrencies have more than doubled in number between 2021 and 2022. Toward the end of 2021, the market added approximately 1,000 new cryptocurrencies per month.
12. What are the different types of Crypto?
Bitcoin (BTC), Ethereum (ETH), Tether (USDT), USD Coin (USDC), and Binance Coin (BNB) are some of the popular ones.
News
An enhanced consensus algorithm for blockchain
The introduction of the link and reputation evaluation concepts aims to improve the stability and security of the consensus mechanism, decrease the likelihood of malicious nodes joining the consensus, and increase the reliability of the selected consensus nodes.
The link model structure based on joint action
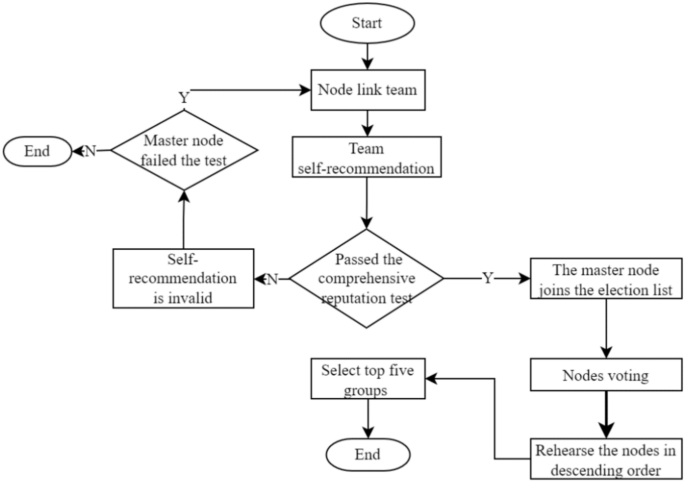
Through the LINK between nodes, all the LINK nodes engage in consistent activities during the operation of the consensus mechanism. The reputation evaluation mechanism evaluates the trustworthiness of nodes based on their historical activity status throughout the entire blockchain. The essence of LINK is to drive inactive nodes to participate in system activities through active nodes. During the stage of selecting leader nodes, nodes are selected through self-recommendation, and the reputation evaluation of candidate nodes and their LINK nodes must be qualified. The top 5 nodes of the total nodes are elected as leader nodes through voting, and the nodes in their LINK status are candidate nodes. In the event that the leader node goes down, the responsibility of the leader node is transferred to the nodes in its LINK through the view-change. The LINK connection algorithm used in this study is shown in Table 2, where LINKm is the linked group and LINKP is the percentage of linked nodes.
Table 2 LINK connection algorithm.
Node type
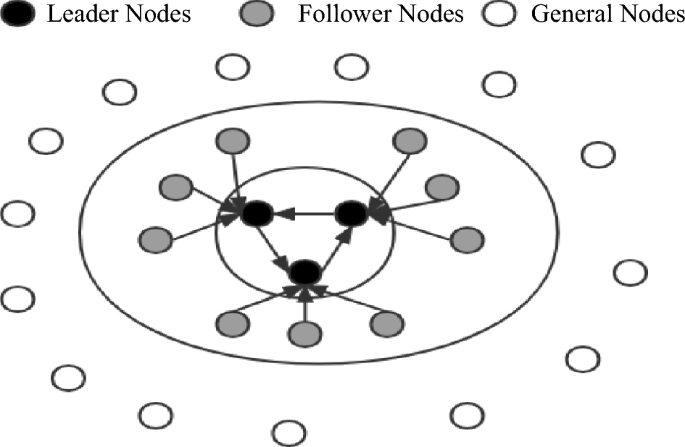
This paper presents a classification of nodes in a blockchain system based on their functionalities. The nodes are divided into three categories: leader nodes (LNs), follower nodes (FNs), and general nodes (Ns). The leader nodes (LNs) are responsible for producing blocks and are elected through voting by general nodes. The follower nodes (FNs) are nodes that are linked to leader nodes (LNs) through the LINK mechanism and are responsible for validating blocks. General nodes (N) have the ability to broadcast and disseminate information, participate in elections, and vote. The primary purpose of the LINK mechanism is to act in combination. When nodes are in the LINK, there is a distinction between the master and slave nodes, and there is a limit to the number of nodes in the LINK group (NP = {n1, nf1, nf2 ……,nfn}). As the largest proportion of nodes in the system, general nodes (N) have the right to vote and be elected. In contrast, leader nodes (LNs) and follower nodes (FNs) do not possess this right. This rule reduces the likelihood of a single node dominating the block. When the system needs to change its fundamental settings due to an increase in the number of nodes or transaction volume, a specific number of current leader nodes and candidate nodes need to vote for a reset. Subsequently, general nodes need to vote to confirm this. When both confirmations are successful, the new basic settings are used in the next cycle of the system process. This dual confirmation setting ensures the fairness of the blockchain to a considerable extent. It also ensures that the majority holds the ultimate decision-making power, thereby avoiding the phenomenon of a small number of nodes completely controlling the system.
After the completion of a governance cycle, the blockchain network will conduct a fresh election for the leader and follower nodes. As only general nodes possess the privilege to participate in the election process, the previous consortium of leader and follower nodes will lose their authorization. In the current cycle, they will solely retain broadcasting and receiving permissions for block information, while their corresponding incentives will also decrease. A diagram illustrating the node status can be found in Fig. 1.
Election method
The election method adopts the node self-nomination mode. If a node wants to participate in an election, it must form a node group with one master and three slaves. One master node group and three slave node groups are inferred based on experience in this paper; these groups can balance efficiency and security and are suitable for other project collaborations. The successfully elected node joins the leader node set, and its slave nodes enter the follower node set. Considering the network situation, the maximum threshold for producing a block is set to 1 s. If the block fails to be successfully generated within the specified time, it is regarded as a disconnected state, and its reputation score is deducted. The node is skipped, and in severe cases, a view transformation is performed, switching from the master node to the slave node and inheriting its leader’s rights in the next round of block generation. Although the nodes that become leaders are high-reputation nodes, they still have the possibility of misconduct. If a node engages in misconduct, its activity will be immediately stopped, its comprehensive reputation score will be lowered, it will be disqualified from participating in the next election, and its equity will be reduced by 30%. The election process is shown in Fig. 2.
Incentives and penalties
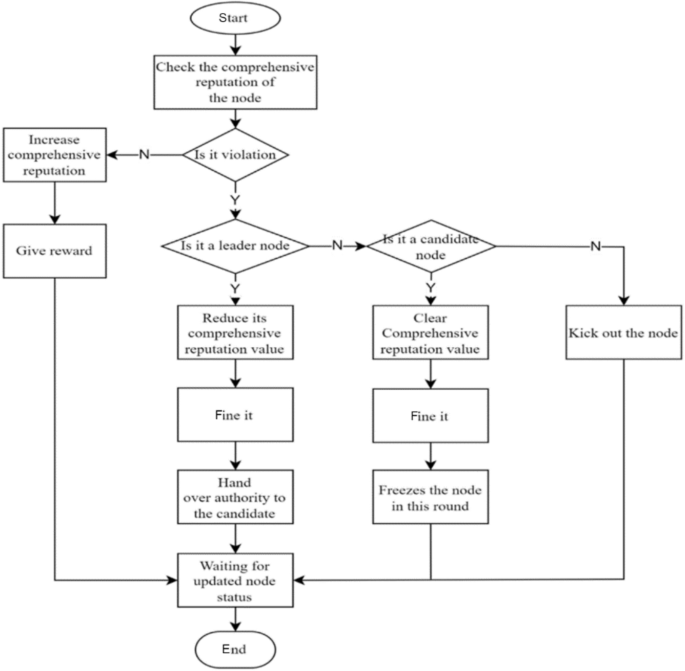
To balance the rewards between leader nodes and ordinary nodes and prevent a large income gap, two incentive/penalty methods will be employed. First, as the number of network nodes and transaction volume increase, more active nodes with significant stakes emerge. After a prolonged period of running the blockchain, there will inevitably be significant class distinctions, and ordinary nodes will not be able to win in the election without special circumstances. To address this issue, this paper proposes that rewards be reduced for nodes with stakes exceeding a certain threshold, with the reduction rate increasing linearly until it reaches zero. Second, in the event that a leader or follower node violates the consensus process, such as by producing a block out of order or being unresponsive for an extended period, penalties will be imposed. The violation handling process is illustrated in Fig. 3.
Violation handling process.
Comprehensive reputation evaluation and election mechanism based on historical transactions
This paper reveals that the core of the DPoS consensus mechanism is the election process. If a blockchain is to run stably for a long time, it is essential to consider a reasonable election method. This paper proposes a comprehensive reputation evaluation election mechanism based on historical records. The mechanism considers the performance indicators of nodes in three dimensions: production rate, tokens, and validity. Additionally, their historical records are considered, particularly whether or not the nodes have engaged in malicious behavior. For example, nodes that have ever been malicious will receive low scores during the election process unless their overall quality is exceptionally high and they have considerable support from other nodes. Only in this case can such a node be eligible for election or become a leader node. The comprehensive reputation score is the node’s self-evaluation score, and the committee size does not affect the computational complexity.
Moreover, the comprehensive reputation evaluation proposed in this paper not only is a threshold required for node election but also converts the evaluation into corresponding votes based on the number of voters. Therefore, the election is related not only to the benefits obtained by the node but also to its comprehensive evaluation and the number of voters. If two nodes receive the same vote, the node with a higher comprehensive reputation is given priority in the ranking. For example, in an election where node A and node B each receive 1000 votes, node A’s number of stake votes is 800, its comprehensive reputation score is 50, and only four nodes vote for it. Node B’s number of stake votes is 600, its comprehensive reputation score is 80, and it receives votes from five nodes. In this situation, if only one leader node position remains, B will be selected as the leader node. Displayed in descending order of priority as comprehensive credit rating, number of voters, and stake votes, this approach aims to solve the problem of node misconduct at its root by democratizing the process and subjecting leader nodes to constraints, thereby safeguarding the fundamental interests of the vast majority of nodes.
Comprehensive reputation evaluation
This paper argues that the election process of the DPoS consensus mechanism is too simplistic, as it considers only the number of election votes that a node receives. This approach fails to comprehensively reflect the node’s actual capabilities and does not consider the voters’ election preferences. As a result, nodes with a significant stake often win and become leader nodes. To address this issue, the comprehensive reputation evaluation score is normalized considering various attributes of the nodes. The scoring results are shown in Table 3.
Table 3 Comprehensive reputation evaluation.
Since some of the evaluation indicators in Table 3 are continuous while others are discrete, different normalization methods need to be employed to obtain corresponding scores for different indicators. The continuous indicators include the number of transactions/people, wealth balance, network latency, network jitter, and network bandwidth, while the discrete indicators include the number of violations, the number of successful elections, and the number of votes. The value range of the indicator “number of transactions/people” is (0,1), and the value range of the other indicators is (0, + ∞). The equation for calculating the “number of transactions/people” is set as shown in Eq. (1).
$$A_{1} = \left\{ {\begin{array}{*{20}l} {0,} \hfill & {{\text{G}} = 0} \hfill \\ {\frac{{\text{N}}}{{\text{G}}}*10,} \hfill & {{\text{G}} > 0} \hfill \\ \end{array} } \right.$$
(1)
where N represents the number of transactional nodes and G represents the number of transactions. It reflects the degree of connection between the node and other nodes. Generally, nodes that transact with many others are safer than those with a large number of transactions with only a few nodes. The limit value of each item, denoted by x, is determined based on the situation and falls within the specified range, as shown in Eq. (2). The wealth balance and network bandwidth indicators use the same function to set their respective values.
$${A}_{i}=20*\left(\frac{1}{1+{e}^{-{a}_{i}x}}-0.5\right)$$
(2)
where x indicates the value of this item and expresses the limit value.
In Eq. (3), x represents the limited value of this indicator. The lower the network latency and network jitter are, the higher the score will be.
The last indicators, which are the number of violations, the number of elections, and the number of votes, are discrete values and are assigned different scores according to their respective ranges. The scores corresponding to each count are shown in Table 4.
$$A_{3} = \left\{ {\begin{array}{*{20}l} {10*\cos \frac{\pi }{200}x,} \hfill & {0 \le x \le 100} \hfill \\ {0,} \hfill & {x > 100} \hfill \\ \end{array} } \right.$$
(3)
Table 4 Score conversion.
The reputation evaluation mechanism proposed in this paper comprehensively considers three aspects of nodes, wealth level, node performance, and stability, to calculate their scores. Moreover, the scores obtain the present data based on historical records. Each node is set as an M × N dimensional matrix, where M represents M times the reputation evaluation score and N represents N dimensions of reputation evaluation (M < = N), as shown in Eq. (4).
$${\text{N}} = \left( {\begin{array}{*{20}c} {a_{11} } & \cdots & {a_{1n} } \\ \vdots & \ddots & \vdots \\ {a_{m1} } & \cdots & {a_{mn} } \\ \end{array} } \right)$$
(4)
The comprehensive reputation rating is a combined concept related to three dimensions. The rating is set after rating each aspect of the node. The weight w and the matrix l are not fixed. They are also transformed into matrix states as the position of the node in the system changes. The result of the rating is set as the output using Eq. (5).
$$\text{T}=\text{lN}{w}^{T}=\left({l}_{1}\dots {\text{l}}_{\text{m}}\right)\left(\begin{array}{ccc}{a}_{11}& \cdots & {a}_{1n}\\ \vdots & \ddots & \vdots \\ {a}_{m1}& \cdots & {a}_{mn}\end{array}\right){\left({w}_{1}\dots {w}_{n}\right)}^{T}$$
(5)
Here, T represents the comprehensive reputation score, and l and w represent the correlation coefficient. Because l is a matrix of order 1*M, M is the number of times in historical records, and M < = N is set, the number of dimensions of l is uncertain. Set the term l above to add up to 1, which is l1 + l2 + …… + ln = 1; w is also a one-dimensional matrix whose dimension is N*1, and its purpose is to act as a weight; within a certain period of time, w is a fixed matrix, and w will not change until the system changes the basic settings.
Assume that a node conducts its first comprehensive reputation rating, with no previous transaction volume, violations, elections or vote. The initial wealth of the node is 10, the latency is 50 ms, the jitter is 100 ms, and the network bandwidth is 100 M. According to the equation, the node’s comprehensive reputation rating is 41.55. This score is relatively good at the beginning and gradually increases as the patient participates in system activities continuously.
Voting calculation method
To ensure the security and stability of the blockchain system, this paper combines the comprehensive reputation score with voting and randomly sorts the blocks, as shown in Eqs. (3–6).
$$Z=\sum_{i=1}^{n}{X}_{i}+nT$$
(6)
where Z represents the final election score, Xi represents the voting rights earned by the node, n is the number of nodes that vote for this node, and T is the comprehensive reputation score.
The voting process is divided into stake votes and reputation votes. The more reputation scores and voters there are, the more total votes that are obtained. In the early stages of blockchain operation, nodes have relatively few stakes, so the impact of reputation votes is greater than that of equity votes. This is aimed at selecting the most suitable node as the leader node in the early stage. As an operation progresses, the role of equity votes becomes increasingly important, and corresponding mechanisms need to be established to regulate it. The election vote algorithm used in this paper is shown in Table 5.
Table 5 Election vote counting algorithm.
This paper argues that the election process utilized by the original DPoS consensus mechanism is overly simplistic, as it relies solely on the vote count to select the node that will oversee the entire blockchain. This approach cannot ensure the security and stability of the voting process, and if a malicious node behaves improperly during an election, it can pose a significant threat to the stability and security of the system as well as the safety of other nodes’ assets. Therefore, this paper proposes a different approach to the election process of the DPoS consensus mechanism by increasing the complexity of the process. We set up a threshold and optimized the vote-counting process to enhance the security and stability of the election. The specific performance of the proposed method was verified through experiments.
The election cycle in this paper can be customized, but it requires the agreement of the blockchain committee and general nodes. The election cycle includes four steps: node self-recommendation, calculating the comprehensive reputation score, voting, and replacing the new leader. Election is conducted only among general nodes without affecting the production or verification processes of leader nodes or follower nodes. Nodes start voting for preferred nodes. If they have no preference, they can use the LINK mechanism to collaborate with other nodes and gain additional rewards.
View changes
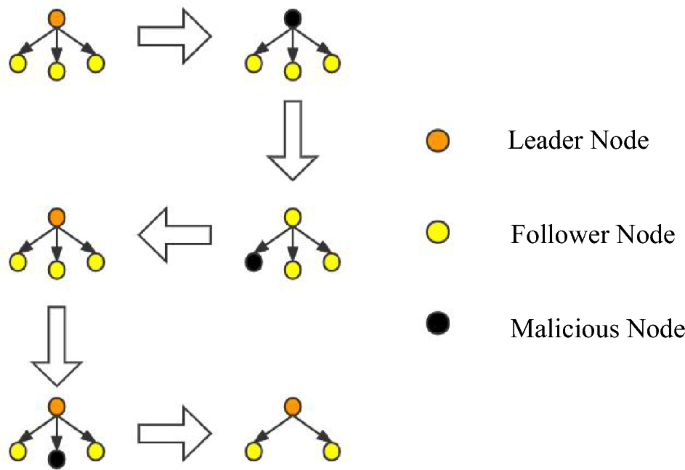
During the consensus process, conducting a large number of updates is not in line with the system’s interests, as the leader node (LN) and follower node (FN) on each node have already been established. Therefore, it is crucial to handle problematic nodes accurately when issues arise with either the LN or FN. For instance, when a node fails to perform its duties for an extended period or frequently fails to produce or verify blocks within the specified time range due to latency, the system will precisely handle them. For leader nodes, if they engage in malicious behavior such as producing blocks out of order, the behavior is recorded, and their identity as a leader node is downgraded to a follower node. The follower node inherits the leader node’s position, and the nature of their work is transformed as they swap their responsibilities of producing and verifying blocks with their original work. This type of behavior will not significantly affect the operation of the blockchain system. Instead of waiting until the end of the current committee round to punish malicious nodes, dynamic punishment is imposed on the nodes that affect the operation of the blockchain system to maintain system security. The view change operation is illustrated in Fig. 4.
In traditional PBFT, view changes are performed according to the view change protocol by changing the view number V to the next view number V + 1. During this process, nodes only receive view change messages and no other messages from other nodes. In this paper, the leader node group (LN) and follower node group (FN) are selected through an election of the LINK group. The node with LINKi[0] is added to the LN leader node group, while the other three LINK groups’ follower nodes join the FN follower node group since it is a configuration pattern of one master and three slaves. The view change in this paper requires only rearranging the node order within the LINK group to easily remove malicious nodes. Afterward, the change is broadcast to other committee nodes, and during the view transition, the LINK group does not receive block production or verification commands from the committee for stability reasons until the transition is completed.
News
The Hype Around Blockchain Mortgage Has Died Down, But This CEO Still Believes

LiquidFi Founder Ian Ferreira Sees Huge Potential in Blockchain Despite Hype around technology is dead.
“Blockchain technology has been a buzzword for a long time, and it shouldn’t be,” Ferriera said. “It should be a technology that lives in the background, but it makes everything much more efficient, much more transparent, and ultimately it saves costs for everyone. That’s the goal.”
Before founding his firm, Ferriera was a portfolio manager at a hedge fund, a job that ended up revealing “interesting intricacies” related to the mortgage industry.
Being a mortgage trader opened Ferriera’s eyes to a lot of the operational and infrastructure problems that needed to be solved in the mortgage-backed securities industry, he said. That later led to the birth of LiquidFi.
“The point of what we do is to get raw data attached to a resource [a loan] on a blockchain so that it’s provable. You reduce that trust problem because you have the data, you have the document associated with that data,” said the LiquidFi CEO.
Ferriera spoke with National Mortgage News about the value of blockchain technology, why blockchain hype has fizzled out, and why it shouldn’t.
News
New bill pushes Department of Veterans Affairs to examine how blockchain can improve its work

The Department of Veterans Affairs would have to evaluate how blockchain technology could be used to improve benefits and services offered to veterans, according to a legislative proposal introduced Tuesday.
The bill, sponsored by Rep. Nancy Mace, R-S.C., would direct the VA to “conduct a comprehensive study of the feasibility, potential benefits, and risks associated with using distributed ledger technology in various programs and services.”
Distributed ledger technology, including blockchain, is used to protect and track information by storing data across multiple computers and keeping a record of its use.
According to the text of the legislation, which Mace’s office shared exclusively with Nextgov/FCW ahead of its publication, blockchain “could significantly improve benefits allocation, insurance program management, and recordkeeping within the Department of Veterans Affairs.”
“We need to bring the federal government into the 21st century,” Mace said in a statement. “This bill will open the door to research on improving outdated systems that fail our veterans because we owe it to them to use every tool at our disposal to improve their lives.”
Within one year of the law taking effect, the Department of Veterans Affairs will be required to submit a report to the House and Senate Veterans Affairs committees detailing its findings, as well as the benefits and risks identified in using the technology.
The mandatory review is expected to include information on how the department’s use of blockchain could improve the way benefits decisions are administered, improve the management and security of veterans’ personal data, streamline the insurance claims process, and “increase transparency and accountability in service delivery.”
The Department of Veterans Affairs has been studying the potential benefits of using distributed ledger technology, with the department emission a request for information in November 2021 seeking input from contractors on how blockchain could be leveraged, in part, to streamline its supply chains and “secure data sharing between institutions.”
The VA’s National Institute of Artificial Intelligence has also valued the use of blockchain, with three of the use cases tested during the 2021 AI tech sprint focused on examining its capabilities.
Mace previously introduced a May bill that would direct Customs and Border Protection to create a public blockchain platform to store and share data collected at U.S. borders.
Lawmakers also proposed additional measures that would push the Department of Veterans Affairs to consider adopting other modernized technologies to improve veteran services.
Rep. David Valadao, R-Calif., introduced legislation in June that would have directed the department to report to lawmakers on how it plans to expand the use of “certain automation tools” to process veterans’ claims. The House of Representatives Subcommittee on Disability Assistance and Memorial Affairs gave a favorable hearing on the congressman’s bill during a Markup of July 23.
News
California DMV Uses Blockchain to Fight Auto Title Fraud

TDR’s Three Takeaways: California DMV Uses Blockchain to Fight Fraud
- California DMV uses blockchain technology to manage 42 million auto titles.
- The initiative aims to improve safety and reduce car title fraud.
- The immutable nature of blockchain ensures accurate and tamper-proof records.
The California Department of Motor Vehicles (DMV) is implementing blockchain technology to manage and secure 42 million auto titles. This innovative move aims to address and reduce the persistent problem of auto title fraud, a problem that costs consumers and the industry millions of dollars each year. By moving to a blockchain-based system, the DMV is taking advantage of the technology’s key feature: immutability.
Blockchain, a decentralized ledger technology, ensures that once a car title is registered, it cannot be altered or tampered with. This creates a highly secure and transparent system, significantly reducing the risk of fraudulent activity. Every transaction and update made to a car title is permanently recorded on the blockchain, providing a complete and immutable history of the vehicle’s ownership and status.
As first reported by Reuters, the DMV’s adoption of blockchain isn’t just about preventing fraud. It’s also aimed at streamlining the auto title process, making it more efficient and intuitive. Traditional auto title processing involves a lot of paperwork and manual verification, which can be time-consuming and prone to human error. Blockchain technology automates and digitizes this process, reducing the need for physical documents and minimizing the chances of errors.
Additionally, blockchain enables faster verification and transfer of car titles. For example, when a car is sold, the transfer of ownership can be done almost instantly on the blockchain, compared to days or even weeks in the conventional system. This speed and efficiency can benefit both the DMV and the vehicle owners.
The California DMV’s move is part of a broader trend of government agencies exploring blockchain technology to improve their services. By adopting this technology, the DMV is setting a precedent for other states and industries to follow, showcasing blockchain’s potential to improve safety and efficiency in public services.
-
 Ethereum11 months ago
Ethereum11 months agoEthereum Posts First Consecutive Monthly Losses Since August 2023 on New ETFs
-

 Regulation11 months ago
Regulation11 months agoCryptocurrency Regulation in Slovenia 2024
-

 News11 months ago
News11 months agoNew bill pushes Department of Veterans Affairs to examine how blockchain can improve its work
-

 Regulation11 months ago
Regulation11 months agoThink You Own Your Crypto? New UK Law Would Ensure It – DL News
-

 Regulation11 months ago
Regulation11 months agoUpbit, Coinone, Bithumb Face New Fees Under South Korea’s Cryptocurrency Law
-

 Regulation11 months ago
Regulation11 months agoA Blank Slate for Cryptocurrencies: Kamala Harris’ Regulatory Opportunity
-

 Regulation11 months ago
Regulation11 months agoBahamas Passes Cryptocurrency Bill Designed to Prevent FTX, Terra Disasters
-

 Regulation11 months ago
Regulation11 months agoIndia to Follow G20 Policy for Cryptocurrency Regulation: MoS Finance
-

 Ethereum1 year ago
Ethereum1 year agoComment deux frères auraient dérobé 25 millions de dollars lors d’un braquage d’Ethereum de 12 secondes • The Register
-

 News1 year ago
News1 year ago“Captain Tsubasa – RIVALS” launches on Oasys Blockchain
-

 News11 months ago
News11 months agoEU supports 15 startups to fight online disinformation with blockchain
-

 Videos1 year ago
Videos1 year agoNexus Chain – Ethereum L2 with the GREATEST Potential?